Partnerships in businesses are vital to success. As your business grows, the support of trusted partners becomes invaluable. Whether your partnerships are with third-party affiliates like suppliers and vendors, these collaborations enhance your business operations and propel you to new heights. Hence, cultivating trust and camaraderie with your partners is essential because they assist you in expanding your company’s competitiveness.
Regardless of the infinite benefits that your partners can provide, it’s crucial to note that some of them can put your company at risk, especially for cyberattacks. Organizations that cater to many customers in the supply chain setting work with hundreds of vendors. So, the more complex your supply chain, the more vulnerable it can be.
According to a study by Finance Online, cybersecurity incidents involving suppliers account for up to 50% of all supply chain disruptions. Cybercriminals exploit vulnerabilities in supply chain vendors to infiltrate targeted organizations, spread malware, and gain unauthorized access to sensitive information.
Limited experience, time constraints, supplier interactions, and perceived costs may deter some from implementing successful cyber risk management techniques. However, these hurdles must be overcome to protect a company’s health, reputation, and client satisfaction.
This article will show you:
- How a Secure Supply Chain Can Prevent Cyberattacks
- Five Steps to Build a Secure Supply Chain
Cyberattacks can be significantly reduced by implementing cybersecurity solutions. One of the ways to do so is for executives to proactively secure the supply chain, a susceptible part of their business operations.
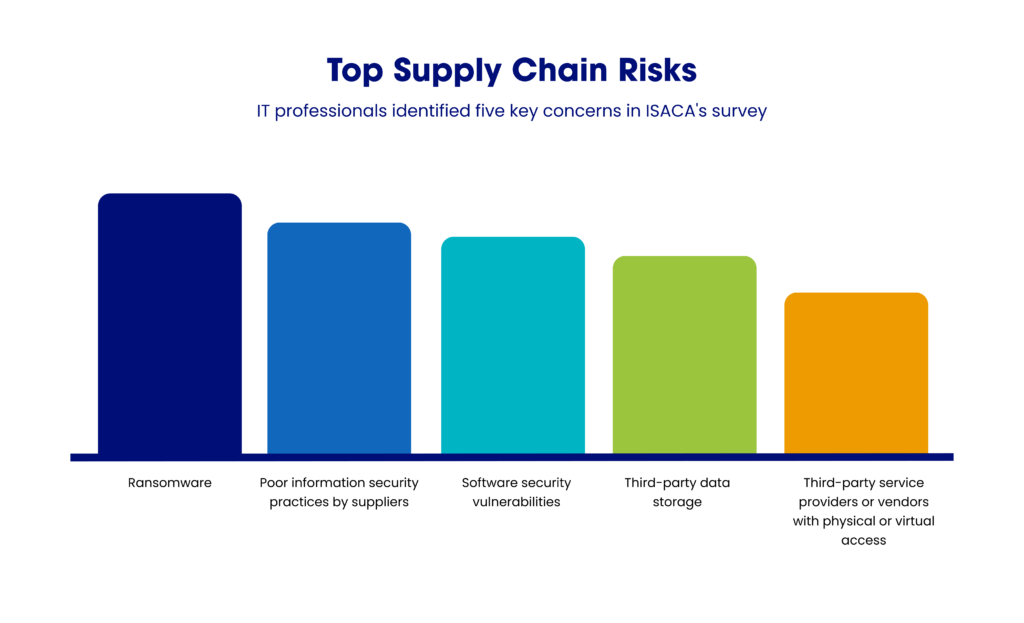
How a Secure Supply Chain Can Prevent Cyberattacks
Depending on the scope of your partnership, some vendors may have access to your critical systems and client information to perform their tasks efficiently. Your company must evaluate and monitor this access to secure your supply chain from potential reputational, legal, or operational risks associated with your suppliers.
Know Your Cyber Risks
External: External cyber threats come from sources other than your company. These cyber-attacks include data breaches, supply chain attacks, ransomware assaults, advanced persistent threats (APTs), and zero-day vulnerabilities. Social engineering is also considered an external threat from outside parties.
Internal: More than your partners and external sources, your staff knows the ins and outs of your infrastructure, cybersecurity measures, and internal threats. According to the 2023 Cost of Insider Threats Global Report, the total cost of insider threats rose from $8.3 million in 2018 to $16.2 million in 2023.
Unfortunately, some employees can be malicious. Your staff can sabotage your business if you have subpar internal security procedures. Poor awareness, including granting unauthorized access or clicking on dubious links, and unintentional data loss or leakages are sources of significant internal risk.
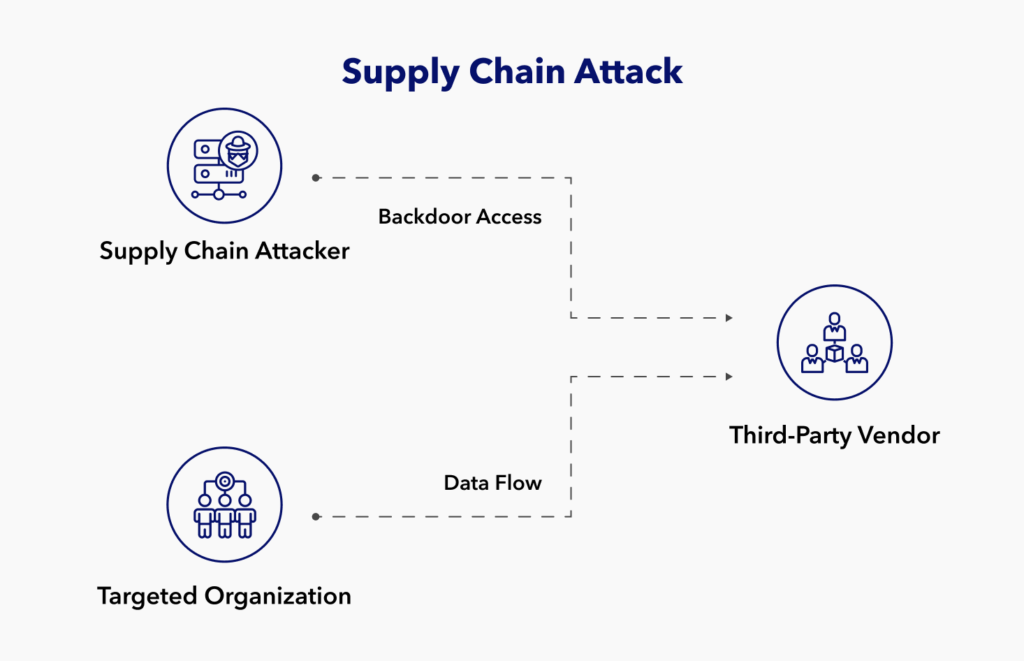
Cyber Risk Management is Essential
Government regulations and a greater reliance on third parties have led to more sophisticated cyber attacks. Hackers have learned to target larger companies indirectly. In the last year alone, third-party data breaches at Boeing, Okta, and AirEuropa have shown how critical it is to upgrade security against external threats.
Third-party risk management uses various techniques, such as cyber security ratings, security questionnaires, and business assessments by an external third party. These are important to help evaluate and manage the risk provided by third-party suppliers.
Traditional third-party risk management, however, has many challenges. Several issues have highlighted the need to automate its processes. Time-consuming, complex security questionnaires and their subjectivity are significant roadblocks to building a secure supply chain.
Another necessity is involving supply chain visibility into operations to have a more calculated view of its inherent risk levels. Some companies use a third-party cyber risk management tool to automatically find, rank, alert, and fix cyber threats.
Five Steps to Build a Secure Supply Chain
Building a robust framework for supplier risk management is crucial to secure the supply chain against the growing threat of cyberattacks. To lay a solid foundation, focus on the three S’s: speed, scope, and scale.
Speed involves assessing, managing, and monitoring risk levels to avoid overburdening internal teams.
Scale ensures maximum visibility for every provider involved in the monitoring process.
Scope sets the cybersecurity risk levels at the onset of engagement.
Security teams must remain vigilant for potential data breaches and related incidents. Here are the following steps to a secure supply chain:
1. Evaluate the security protocols of your suppliers.
When you start working with a supplier or vendor, conduct third-party risk assessments to understand the potential threats they may pose to your supply chain. This process involves developing key risk indicators (KRIs) to monitor metrics such as the number of identified risks, the proportion of risks under observation, those that have materialized, and those that have been mitigated.
2. Set non-negotiable security requirements.
An effective cyber risk management strategy involves communicating security and compliance standards to third parties. These requirements are critical elements of a robust cybersecurity plan. They should include access controls, employee awareness and training, data encryption levels, accident response protocols, and adherence to relevant regulations such as GDPR and HIPAA.
You must conduct regular audits and evaluations of the third party’s compliance to ensure these standards are met and remain effective.
3. Implement an incident response plan.
When it comes to cyber attacks, it’s not a question of if but when. The first step to reduce the impact of a cyber attack is enabling your company and the supplier to respond proactively during a supply chain or third-party threat.
With the help of external experts, incorporate attack simulations into your incident response strategy. These controlled exercises provide valuable insights and allow you to refine your response plan, making adjustments that enhance your defenses against similar attacks in the future.
4. Be vigilant and constantly monitor potential risks
The cybersecurity environment and your attack surface are continually changing. There’s a lot to track when you rely on third-party applications, services, IoT devices, partners, and suppliers. Even after onboarding and due diligence processes, over 80% of third-party services still have security risks, according to a study by Gartner.
You must constantly monitor your third parties’ digital footprints and assets visible to the outside world. External attack surface monitoring identifies possible weak points that outside hackers and unauthorized users could exploit.
A secure supply chain goes beyond initial onboarding and due diligence. Continuous risk monitoring also includes evaluating the effectiveness of existing security measures.
Conclusion
Businesses need to build a secure supply chain to stay resilient. Solid backup plans and regular supplier audits and inspections must support this. They also need a comprehensive defense strategy to be prepared for constantly changing cyber-risk scenarios.
Take a proactive approach to responding to the increasing supply chain interruptions caused by cybersecurity events to prevent severe financial losses and reputational damage. Aratum serves as the foundation for a secure supply chain. Augment your cyber security protocols with supply chain management software. Coordinate with suppliers faster and verify sensitive transactions in real time . Jadwalkan demo now.
The featured photo of this article was sourced from freepik.
