Imagine a network of companies collaborating to produce and provide the goods and services we depend on, much like a well-oiled machine. That is how the modern supply chain works.
Every link is necessary for the entire system to function like a machine. Each organization contributes differently to the complex movement of supply and demand that keeps the network alive and well.
Furthermore, thanks to technological breakthroughs, supply networks operate faster and more effectively. Enterprises’ increasing integration and reliance on technology have led to the persistent risk of supply chain attacks.
- Be in the Know: 2024 Supply Chain Cybersecurity Trends
- Staying Protected: Supply Chain Cybersecurity Best Practices
Supply chain attacks are cyberattacks against third-party suppliers inside your company’s supply chain. In the past, these attacks simply exploited trust relationships directed towards unstable providers. This is so malicious parties could attempt to access their bigger partners.
Even if conventional supply chain assaults are still a problem, businesses are now more vulnerable to threats from the software supply chain. Most modern software in use today is not custom-made. It includes many off-the-shelf components, including third-party APIs, open-source code, and proprietary code from other software vendors to cut costs. These factors and some software features make supply chain software more vulnerable to attack.
A software supply chain attack can insert malicious code into an application and infect its users. Compare this to a hardware supply chain attack that compromises physical components and uses them to penetrate an organization’s systems. No matter how they are carried out, supply chain attacks can disastrously affect your business and clients.
In recent years, regulatory bodies have pressed businesses to improve cyber risk management for their supply chains. As a result, more companies and their subcontractors must update their risk management protocols.
Poor handling of supply chain cybersecurity can result in medium—to long-term commercial consequences. Data breaches and system disruptions can impact your brand, resulting in a poor reputation and reduced customer loyalty.
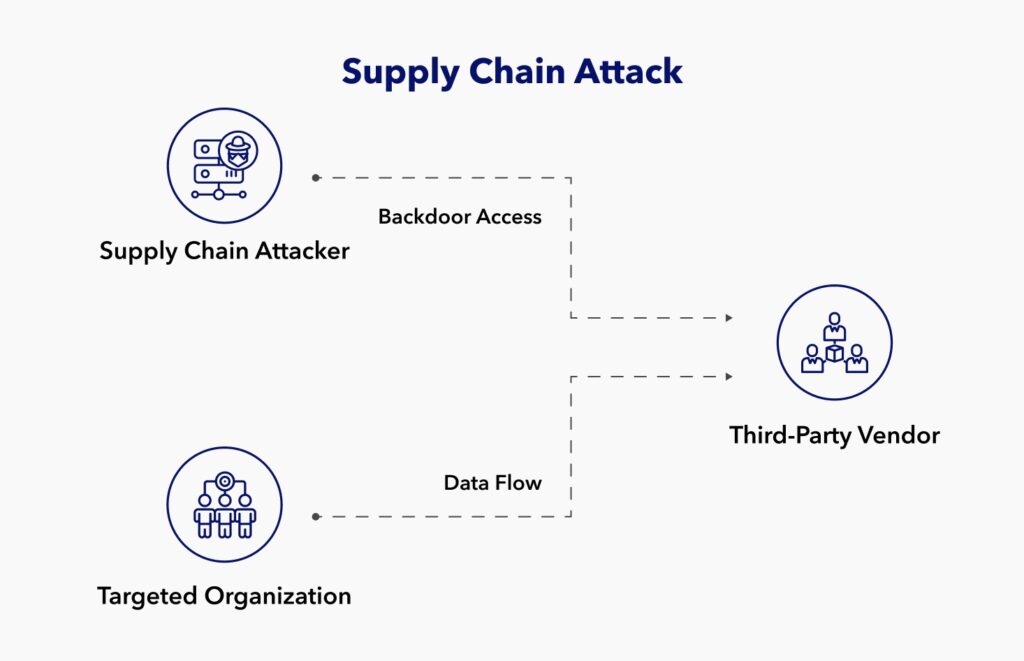
Even established multinational companies aren’t safe from cyberattacks. Take, for example, the SolarWinds supply chain attack. Hackers introduced a backdoor into a SolarWinds software update. Several high-profile businesses and government organizations use SolarWinds’ networking product. The backdoor enabled attackers to access thousands of government and business servers remotely. The worldwide attack caused numerous security issues and data breaches. On average, the attack cost companies 11% of their annual revenue.
Cyberattacks will only become more common as supply chains become more complex and increasingly dependent on technology. Here are some supply chain cybersecurity risks your team should focus on in 2024.
Be in the Know: 2024 Supply Chain Cybersecurity Trends
Cybersecurity budgets are expected to increase by an average of 6% in 2024. However, despite having more funding, cyber security experts can’t track every cyber threat out there. There are way too many potential risks for a company to handle simultaneously. One way to handle this problem is to identify some key trends and the related dangers that are most likely to happen. By understanding their significant impact, you can have direction and purpose for your supply chain cybersecurity strategy.
1. Social Engineering Attacks
People remain the weakest link in an organization’s security due to their tendency toward common human mistakes and behaviors. Threat actors will continue to attack people in 2024, regardless of how strong the regulations are and how safe the organizations’ systems are.
Phishing continues to be the most common attack vector, with over 700 social engineering attacks against businesses yearly. ENISA identifies the following as other popular social engineering threats: spear-phishing, whaling, smishing, vishing, watering hole attacks, baiting, pretexting, quid pro quo, honeytraps, and scareware.
Employees find it harder to recognize phishing emails, texts, or LinkedIn messages. Social engineering attacks have become more sophisticated. As a result, they may unintentionally click on a malicious link or download a corrupted document. Spoofing is the most common phishing assault, in which a threat actor assumes the identity of a reliable company, partner, customer, or coworker. Generative AI will make spoofing even more challenging to detect. It will enable threat actors to craft far more personalized messages, utilizing deep fakes in audio and visual form.
2. Generative AI
Generative AI offers many benefits, but it also comes with its own set of risks. Security teams can benefit from its sophisticated data analytic capacity, which will lessen their workload. The AI can improve threat intelligence and analysis, early detection, incident response, smart authentication, and other operations.
However, hackers are also extensively using these new tools. AI is mainly used to create and improve more difficult-to-detect malware. Businesses using generative AI applications can make corporate data availability, confidentiality, and integrity vulnerable.
Generative AI and language learning models (LLMs) are vulnerable to hacking techniques such as denial of service attacks, inference assaults, data poisoning, and prompt injection attacks. However, because they tend to provide erroneous information and have “hallucinations,” they may also be a risk to organizations. Finally, staff members could enter confidential or client information into these programs, opening it up to possible unauthorized access.
3. Exploiting weak links in the extended supply chain
One of the biggest threats to a company’s supply chain cybersecurity is concentrated risks beyond your immediate suppliers and third-party vendors. An example is when businesses lack backup plans and rely only on a single provider for any business-critical functions or services.
Business continuity could be threatened if an organization entirely depends on a crucial supplier and does not have a backup provider. If the supplier breaches and goes down, it will have a whiplash effect across the entire chain.
Reliance on these “fourth-party” organizations makes your business vulnerable to systemic risk. If one or more of your suppliers rely on the same source for materials, any disruption could cause supply chain failure.
Staying Protected: Supply Chain Cybersecurity Best Practices
Preventing cyberattacks before they happen is the best method for handling them in your supply chain networks. Cybersecurity breaches are mainly caused by human error. Even with the technological complexity of widespread cyber assaults on supply chain networks, they can still happen. A crucial line of defense is raising knowledge about information security.

Data encryption
Encryption procedures should be applied to all data types. Businesses must focus on the interface of third-party integrations to reduce the value of sensitive data in case of a third-party attack. Ideally, AES—the Advanced Encryption Standard—should be used. It’s widely regarded as one of the most challenging encryption types to crack. Militaries and governments around the world frequently use it because of its security.
Secure employee credentials and access
Many crippling cyberattacks have been caused by a single mistake. One bad email link or virus download is enough to expose your supply chain. Make sure your users understand the significance of password and login security. These security measures are your first line of defense for preventing cyberattacks and enhancing supply chain resilience. Provide training and assessments to staff so they can recognize malware, safeguard software and devices, and spot phishing emails.
Information campaigns
Relatively unimportant information is not easily retained or used by anyone. Create scenarios showing how cyberattacks affect different employee positions, the company, and supply chain partners. Provide your personnel with tools and training to help them become more familiar with supply chain cybersecurity. Regularly update your team with the latest attack tactics.
Penetration testing
Thanks to vulnerability scanning, low-level vulnerabilities can be found early. Findings may also be used to update weak passwords, ensure better, more secure database setups, and safeguard endpoints and networks.
Vulnerability mitigation provides early gains that lower risk without causing downtime or obstructing production. After the security team has addressed the fundamentals, a penetration testing specialist or team may assist in locating more sophisticated supply chain risks. Finding the weak links can enhance the security system as a whole.
Have an incident response plan ready
It is important to have a strong incident response strategy to be ready for security breaches, system outages, or other interruptions. A tested, workable, simple-to-implement reaction strategy may reduce revenue losses, reputational harm, and partner or customer attrition rates. Be sure to include deployable remediation actions with this plan.
Security intelligence and response planning provide the metrics for internal teams and external partners to make well-informed decisions to avert future assaults.
Strengthen your internal network
Efficient internal supply chain management is critical for successfully delivering the finished product to customers. Without raw materials from external suppliers, your company cannot make goods. Nonetheless, internal procedures will decide whether the finished product is fit for sale.
Meticulous planning is a key element influencing the performance of the internal supply chain. It lets you decide how best to develop and market your product and guarantees that manufacturing will happen by the deadline. For a pipeline to be effective, operations need to be optimized through careful planning.
Your supply chain and internal network can be more secure and optimized to help you meet customer requests, manage unforeseen problems, and maintain employee satisfaction. But extensive visibility management is also necessary.
Due to the rapidly changing risk environment, businesses must modify and improve their supply chain cybersecurity protocols in 2024. Organizations must proactively handle new risks. Doing this will enhance resilience and uphold stakeholder confidence in an increasingly linked business environment. Staying up-to-date with the latest trends in cybersecurity is the first step to a better-protected supply chain.
Aratum simplifies complex supply chain management. Our software gives you greater oversight and visibility over your suppliers and partners. Identify problems before they get worse and communicate action plans seamlessly. Book a demo to learn how to strengthen your supply chain cybersecurity plans.
The featured photo for this article was sourced from rawpixel.com on freepik.



