While technological advancements offer marvelous contributions to society, there are ironic challenges to it, especially regarding data security. As more people get access to tech upgrades, more individuals are also compromised digitally. According to a report by AAG, data breaches and cyber-attacks increased by 168% in the Asia Pacific alone. This alarming surge indicates the pervasive and escalating risks that companies face in safeguarding sensitive information. It underscores the need for enhanced cybersecurity measures to mitigate the threats.
Several innovations have made it possible for computer systems, devices, applications, companies, government facilities, and households to dig into several security measures. From passwords and patterns to fingerprint security scans, companies try to deploy each, as one that preceded the other lacks in giving us full-on protection. Now enter Facial Recognition Security.
The Rise of Facial Recognition Security Camera System
In the mid-1960s, scientists led by Woodrow W. Bledsoe began exploring the concept of using computers to recognize human faces. It was a challenging feat, especially since it was hard for computers to imitate the ability to distinguish faces. However, in 2006, the National Institute of Standards and Technology (NIST) revealed that machine recognition has improved multifold after a test. In fact, the best recognition systems at that time outperformed many humans in accuracy.
Since that breakthrough, facial recognition has continually improved and is now known as one of the most progressive technologies in the world. Its acceptance and use have expanded beyond security and law enforcement.
Along with the rise of 3D modeling and real-time image capture, the latest facial recognition security camera systems can identify distinctive features such as the curves of the eyes, nose, and chin. The growth of facial recognition security was fueled by hardware advancement, as well as innovative strategies of measurement and analysis. Facial recognition is now a crucial part of our technology-driven world, but what makes it unique from other security systems?
Facial Recognition Security System is a Game-Changer
Among all the security systems today, facial recognition security camera systems stand out for several compelling reasons. First, it has biometric precision that reaches mind-blowing levels, recognizing curves, eye distance, cheekbone shape, and nose width.
Secondly, facial recognition security camera systems eliminate tedious authentication steps many users experience today, including physical tokens and two-factor authentications. It also rids the user of physical contact for pattern recognition and fingerprint scans, which is a main concern for many, especially after the COVID-19 pandemic fiasco. On the other hand, facial recognition security has only one step: for the user to simply be present.
Faces are difficult to imitate; only top security and law enforcement entities like the FBI and CIA have access to face forgery prosthetics. There is even no guarantee that they can pass advanced facial recognition technologies. That’s why your company can be certain about the security that facial recognition security camera systems can provide.
The Features and Advantages of Aratum’s Facial Recognition Security Camera System
Aratum’s facial recognition security camera system solution leverages a cutting-edge AI engine tailored to enhance users’ security and convenience. This technology responds to complex security systems and the growing need for improved authentication.
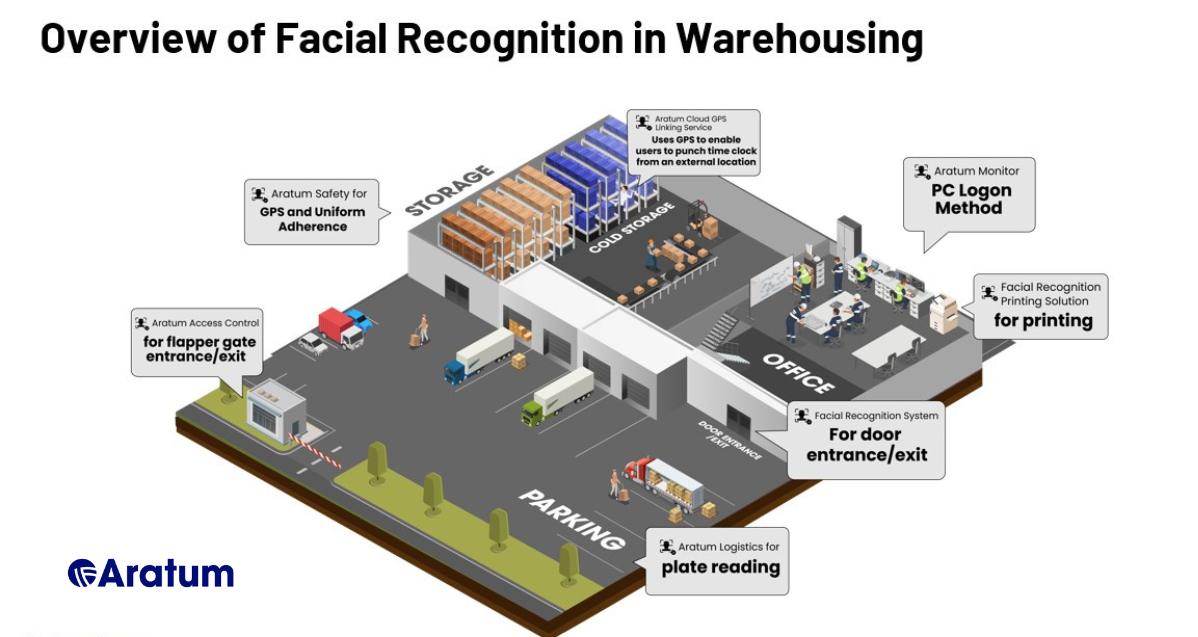
Security at Entry and Exit Points: At the entry point, the facial recognition security camera system terminal combines hardware and software components for seamless entry and exit authentication. Recognizing faces from registered databases and video data, the Aratum access control enhances security upon entrance, which also allows hands-free access and prevents unauthorized use of ID cards.
The system also encompasses server-based software, maintenance services, and compatibility with various entry/exit scenarios. The software goes beyond authentication, as it also features VIP client confirmation and new people who need to enter a facility or use a machine. Aratum’s package provides a flexible and cost-effective solution.
Online and application access: Our facial recognition camera system enables facial recognition for PC logins and application access, which eliminates the need for complex passwords. Equipped with anti-spoofing features and dual-factor authentication, it improves online security while simplifying the user login experience.
Printing systems: One of the additional company expenses is assets such as printers. Your company can control its usage and expense by implementing facial recognition in your printing systems. We offer hands-free user identification to prevent unauthorized access to printers and printed documents.
See
Cloud GPS Tracking: The system goes beyond offices and warehouses. We built in real-time data to capture accurate user information. Say goodbye to the traditional time clock system as we provide accurate tracking of employees and partners.
Data Management Services and Data Sharing: Aratum’s security software allows facial data to be shared across different recognition systems. Thus reducing administrative burdens and enhancing flexibility for the whole company, as well as its partners. It allows administrators to manage face data based on groups and link multiple systems to streamline data sharing and usage.
Privacy and Ethical Considerations
Facial recognition security camera systems have sparked controversies and debates about privacy and ethical concerns, which comes as no surprise due to its potential to intrude into personal lives. Deploying the security system in public raises fears of constant surveillance and leads to loss of privacy and anonymity. Issues about the misuse of collected facial data, such as identity theft, unauthorized tracking, and profile creation without consent, are also of great concern.
Apart from that, ethical issues arise regarding the biases that may be embedded in the technology, and some facial recognition security systems may be inaccurate, especially when trained on biased data.
Aratum’s Priority: Protection and Security
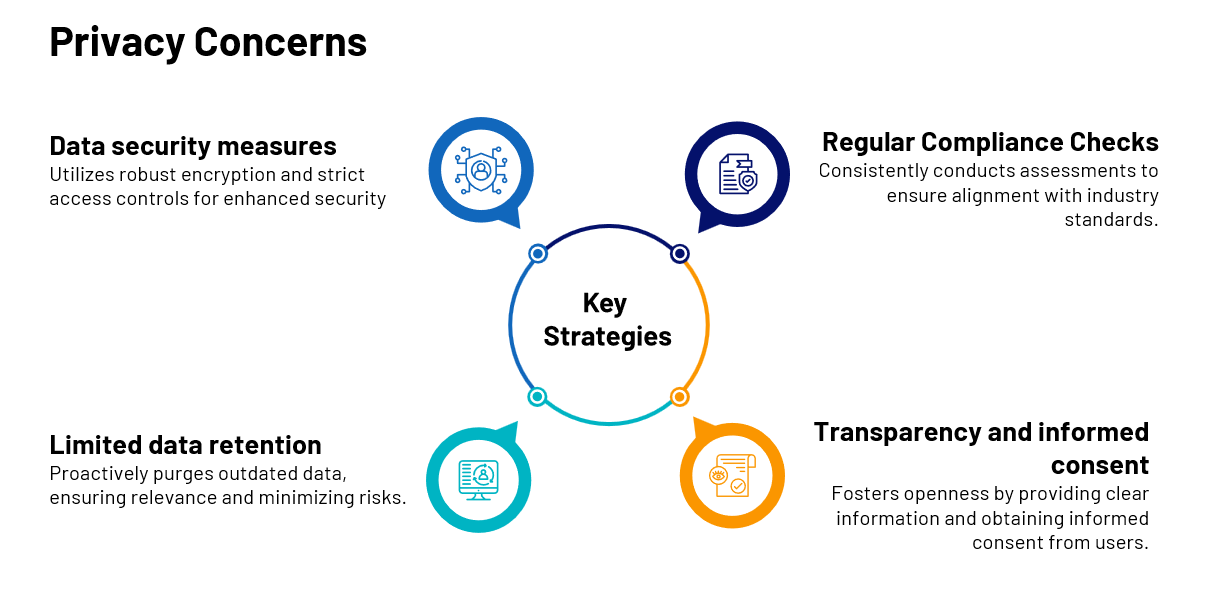
Deploying Aratum’s face recognition security camera system solution addresses these concerns with our commitment to responsible and transparent implementation. We prioritize privacy by adhering to stringent data protection practices. We ensure that all facial data is securely handled, stored, and accessible only to authorized personnel. We strongly emphasize mitigating bias in its algorithms and employing ethical cloud-based ideals to minimize inaccuracies. The company is dedicated to compliance with privacy regulations and industry standards. Lastly, we constantly update our practices to align with evolving ethical norms.
Aratum’s Facial Recognition security camera system stands out as a trustworthy option for businesses. We combine cutting-edge, top-notch facial recognition security capabilities with a principled approach to privacy and ethics. We offer a solution that not only addresses concerns but also sets a benchmark for responsible deployment. See it in action.
The featured photo of this article was sourced from freepik.
Book A Demo Today